AR IPSEC與CISCO IPSEC對接,CISCO采用動态模闆形式
2014/10/12 13:26:21點擊:
問題描述
Cisco設備作(zuò)為總部,AR作(zuò)為分支設備,cisco采用動态模闆的方式創建map。同時(shí)使用ip的方式進行(xíng)協商。

告警信息
無
處理(lǐ)過程
AR設備的配置
# acl number 3000
rule 10 permit ip source 4.4.4.4 0
#
ipsec proposal 1
#
ike proposal 1
#
ike peer vpn1 v1
exchange-mode aggressive
pre-shared-key simple huawei123
ike-proposal 1
remote-address 192.168.2.2
#
ipsec policy vpn1 10 isakmp
security acl 3000
ike-peer vpn1
proposal 1
#
interface GigabitEthernet0/0/0
ip address 192.168.1.2 255.255.255.0
ipsec policy vpn1
Cisco設備的配置
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key huawei123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set TRANS01
esp-des esp-md5-hmac
!
crypto dynamic-map vpn 10
set transform-set TRANS01
match address 102
!
crypto map vpn2 10 ipsec-isakmp dynamic vpn
!
access-list 102 permit ip any host 3.3.3.3
access-list 102 permit ip any host 4.4.4.4
! interface GigabitEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
media-type rj45
crypto map vpn2
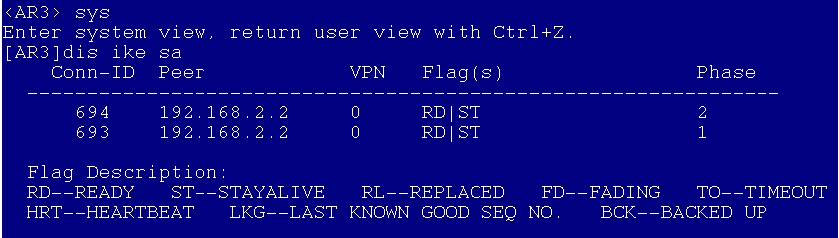
AR的ike sa:
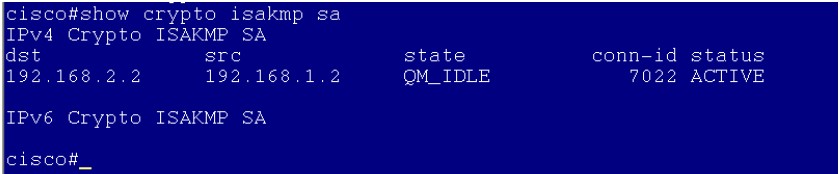
Cisco 的ike sa:
# acl number 3000
rule 10 permit ip source 4.4.4.4 0
#
ipsec proposal 1
#
ike proposal 1
#
ike peer vpn1 v1
exchange-mode aggressive
pre-shared-key simple huawei123
ike-proposal 1
remote-address 192.168.2.2
#
ipsec policy vpn1 10 isakmp
security acl 3000
ike-peer vpn1
proposal 1
#
interface GigabitEthernet0/0/0
ip address 192.168.1.2 255.255.255.0
ipsec policy vpn1
Cisco設備的配置
!
crypto isakmp policy 10
authentication pre-share
crypto isakmp key huawei123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set TRANS01
esp-des esp-md5-hmac
!
crypto dynamic-map vpn 10
set transform-set TRANS01
match address 102
!
crypto map vpn2 10 ipsec-isakmp dynamic vpn
!
access-list 102 permit ip any host 3.3.3.3
access-list 102 permit ip any host 4.4.4.4
! interface GigabitEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
media-type rj45
crypto map vpn2
AR的ike sa:

Cisco 的ike sa:

根因
無
建議與總結
思科動态策略圖就是目前AR所支持的總部采用模闆方式,如果總部采用模闆方式,此時(shí)總部是完全被動接受分支的主動協商的,這種方式可(kě)以支持分支地址為動态地址的場(chǎng)景。本案例中分支地址是确定的,AR采用野蠻模式的IP方式與思科進行(xíng)對接。在采用模闆的場(chǎng)景中,如果思科作(zuò)為總部,需要配置ACL,而如果AR作(zuò)為總部,ACL會(huì)自動生(shēng)成,無需配置。當然該場(chǎng)景如果采用主模式也可(kě)以對接成功,思科不區(qū)分主模式和(hé)野蠻模式。
- 上(shàng)一篇:AR G3路由器(qì)在初始配置環境下是否可(kě)以通(tōng)過Telnet 方 2014/10/12
- 下一篇:AR G3路由器(qì)支持哪些(xiē)方式的NAC 2014/10/12
